Virtual Time
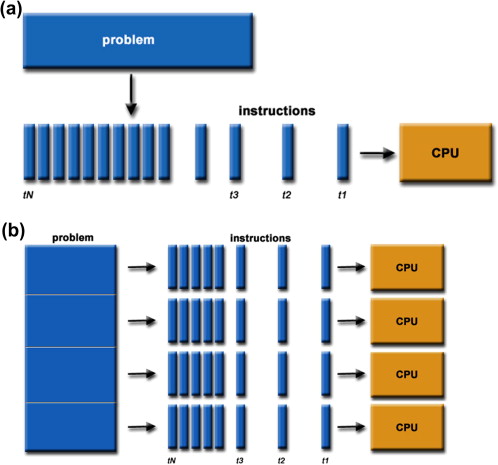
Virtual Time is a subject I studied in my early days right out of college. It’s a concept we explored while thinking about the biggest problem computer processing would eventually experience: the speed of the electron. No matter how short the distance you make between two elements that process data, you will find the bottleneck […]